Digital Detection
- Published: July 01, 2009, By By Roland Meylan, AlpVision SA
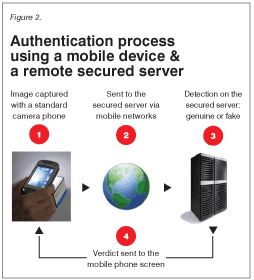
Online digital authentication uses a direct link between a brand product examiner and a secured computer that automatically performs a “genuine or fake” verdict. This provides an instant warning if fakes are uncovered, enabling brand owners to react rapidly to combat defrauders. Today, low-cost consumer electronics devices (flatbed scanners, cell phones, digital cameras, etc.) can be used by anyone to authenticate genuine items from fakes worldwide.
Digital & Sensory Authenticators
Protecting the packaging and labeling of branded products against counterfeiting or fraudulent reimportation can be performed using the following two main approaches:
- Add a feature to the package or label that will be revealed using one or more of the human senses, with or without the aid of a tool. Such a feature will require specific education for the examiner in order to provide the necessary knowledge and expertise to make a reliable determination. Typical examples are holograms, kinegrams, optical variable ink, microprints, ultraviolet ink, etc. These features are called sensory authenticators.
- Add a digital feature to the package or label that is machine readable. Authentication will be performed without human intervention but with the use of a low-cost office scanner and some computing power. If the computer is remote, the authentication process will be online via data networks. Typical examples are an encrypted two-dimensional matrix code, a covert marking, an encrypted serialization, etc. These features are called digital authenticators.
In considering one or the other approach, the brand owner first should identify its defrauder target and define who is going to perform the authentication process. If just a handful of people are in charge of authenticating products, a sensory authenticator could be suitable.
The examiners will cumulate the necessary expertise based on cases, using sight and smell, or even tactile senses for raised intaglio printing, for example. But if a large number of people will be in charge of performing authentications, the problem of how to educate them, update their knowledge, and manage turnover will be difficult to solve and will affect the reliability of the genuine or fake determination.
In this case, a digital authenticator will be easier to implement, as it is based on processes and not on knowledge. The verdict is the result of a software computation, which could be improved infinitely. These improvements then will be available instantly worldwide for anyone authorized to use the authentication process.
Online digital authenticators also provide an important feature — the instant consolidation of all the verdicts performed worldwide, which allows the immediate correlation with supply chain data stored in the product management system of the brand manufacturer. This will lead to the rapid and automatic uncovering of fraudulent importers or retailers, enabling the brand manufacturer to react quickly.
Using sensory or off-line digital authenticators will not provide this instant consolidation of suspicious items. It would then leave the brand owner in the dark as to where the counterfeits are located and how many suspicious items are around.
It is well known that the time elapsed between when a criminal act is committed and when it's uncovered is crucial to combating crime. This is also true for counterfeiting. A worldwide anticounterfeiting program using a high-level covert security feature and online digital authentication could be seen as the most efficient tool if it is cost effective and compatible with large-scale industrialization constraints.
Tools Are Readily Available
Today, being connected via cell phones, mobile networks, WiFi-free services, or fixed Internet connection is common. For example, there are more than 3 billion cell phones worldwide, 1 billion of which are equipped with digital cameras.1 More than 1 billion people are Internet connected, not to mention people using the free WiFi services that are multiplying in public areas and shopping malls. Connected SOHO (Small Office, Home Office) businesses are multiplying, equipped with webcams or flatbed scanners and other low-cost peripherals.
All of these devices are capable of shooting high quality photos and transmitting them with a mouse or finger click. Today, anyone from a small child to a grandparent can shoot a family portrait and send it or publish it on the Internet. This is enough knowledge to perform a digital “genuine or fake” authentication.
Page 2 of 2
Invisible Marking
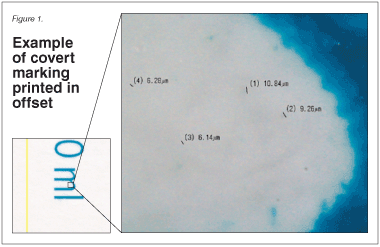
A patented covert marking system that uses normal ink (color, black and white, or varnish) can be applied to primary and secondary packaging and labels.2 Paperboard cartons, aluminum foil, and polymer-laminated foils can be used. Offset, rotogravure, flexography, inkjet, etc., can be used. No modification of the printing process is required, and the production speed is not altered.
The key feature is the printing of a pattern of thousands of microdots (10-50 microns) generated by a digital key of 128 bits and invisible to the naked eye. If a varnish layer is used, microholes are generated instead of dots.
The entire surface of the package or label can be marked without modifying the original design and without modifying the production process. Therefore the covert marking does not incur extra production costs.
To identify a product as genuine or fake, it is necessary to reveal only the presence or the absence of the invisible marking on the package or label. If the covert marking is present, the product is genuine. If the covert marking is absent, the product is a fake. The automatic identification of the microdots or microholes pattern, using the 128-bit secret key, will uncover the production batch.
Anyone can perform an online digital authentication following a step-by-step process, with the help of an online “wizard” if needed. No specific knowledge is necessary.
Brand product manufacturers that adopt such a solution may open the process to various partners, such as overland transport companies (to help them avoid transporting fake products taken in good faith as genuine), customs and legal agents, retailers, and (why not?) consumers. This takes into account the nonreversible development of online shopping.
Digital online authentication is a key weapon to help eradicate the counterfeiting of consumer goods for the best profit of the brands and their consumers worldwide.
Supplier Info
AlpVision SA | www.alpvision.com
Circle 350 or visit www.freeproductinfo.net/pff
Roland Meylan is co-founder and corporate communications manager of AlpVision SA, Vevey, Switzerland. He can be reached at +41 21 922 6124 or This email address is being protected from spambots. You need JavaScript enabled to view it.; www.alpvision.com.
-
The Mobile Phone Industry Figures, Mobile Commerce Opportunities and Challenges, p11. http://www.gs1.org/docs/mobile/GS1_Mobile_Com_Whitepaper.pdf
-
Cryptoglyph Digital Security Solution http://www.alpvision.com/cryptoglyph-covert-marking.html
The views and opinions expressed in Technical Reports are those of the author(s), not those of the editors of PFFC. Please address comments to the author(s).